Nmap - Intermediate
TOOLS
10/25/20222 min read


In this blog, we are going to discuss about the various ways of port scanning using Nmap. It includes fast scanning, port range scanning, software version detection etc.
Port Scanning
It helps you to access the more specific targeted hosts, than default scan approach. By default nmap scans all the TCP ports (1-65535). This slows down the scanning processes.
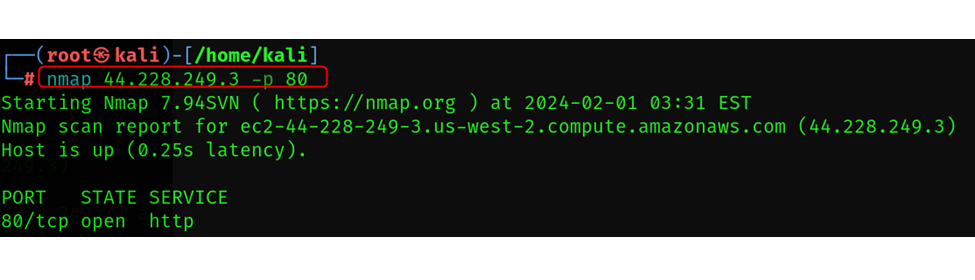
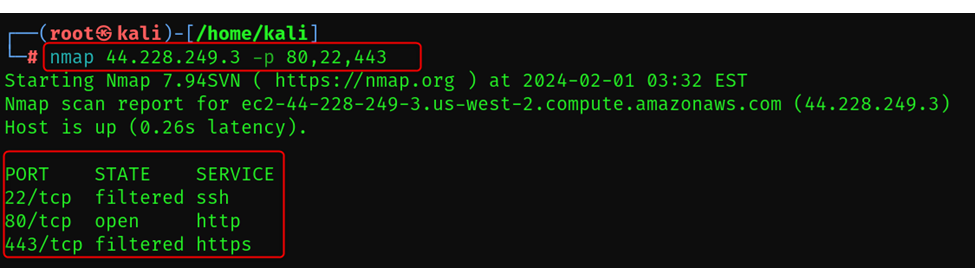
With -p
It helps you to define specific ports, you can enter the ports number that you need by using the comma separated value focusing on you need.
For e.g. nmap -p 22,80,443
Advantages
Speed: Scanning fewer ports significantly reduces scan time, especially on large networks.
Precision: Targeting specific ports helps you find what you're looking for faster and avoids irrelevant information.
4.2 -F (Fast Scan mode)
It provides the faster scan by lower down the number ports, by limiting it to the 1000 popular ports.
With -F:
Nmap focuses on only the 100 most common ports in each protocol, significantly reducing the scan time. This gives you a quick results of open ports likely essential services like web servers, mail servers, and SSH.
Advantages
It provides faster scan, which is good when scanning larger networks.
It provides more efficiency and bandwidth.

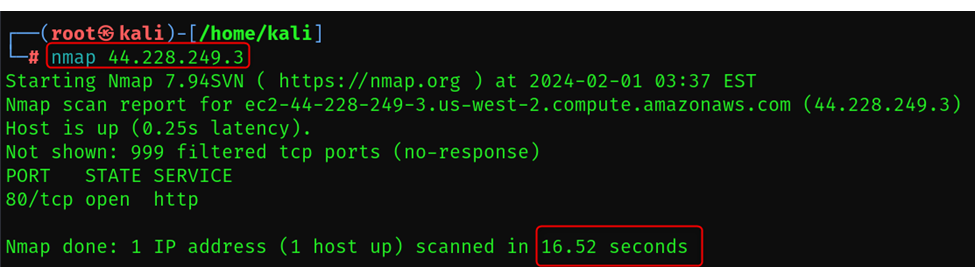
Screenshot with difference between normal scan and fast scan
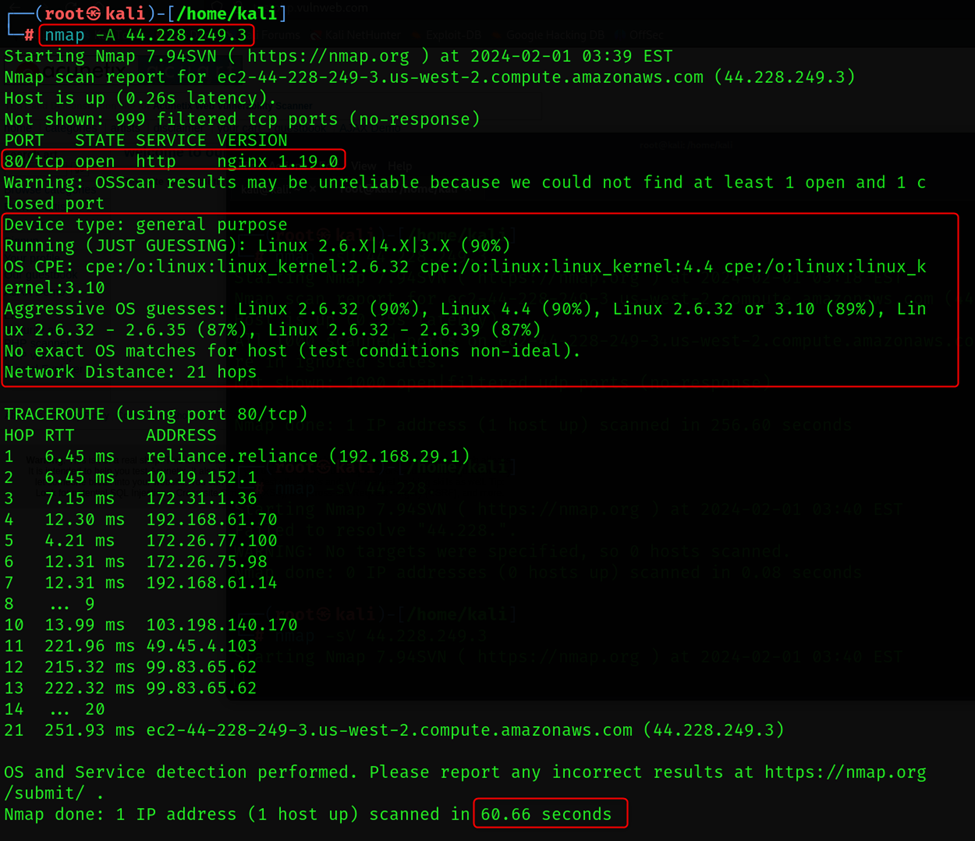
-A (Aggressive scan)
It is uses tool full potential for in-depth analysis.
It includes different types of scans such as OS detection, Version detection and Script Scanning.
With -A:
-A activates an array of additional checks and probes, including:
Script scanning: Executes Nmap scripting engine (NSE) scripts for vulnerability detection and further service probing.
Trace routing: Maps the network path to the target host.
Operating system fingerprinting: Analyses network responses to identify the specific OS version.
Version detection: Provides detailed information about software versions running on open ports.
This aggressive approach provides a highly detailed picture of the target network and its potential vulnerabilities.
Advantages
Thoroughness: -A leaves no stone unturned, uncovering hidden aspects of the network compared to basic scans.
Security assessment: Ideal for security audits, identifying vulnerabilities and potential attack vectors.
In-depth analysis: Provides detailed information about services, versions, and underlying systems.
Time-consuming: -A scans can be significantly slower due to the extensive checks and probes involved.
Resource intensive: Consumes more bandwidth and processing power compared to basic scans.
Disadvantages
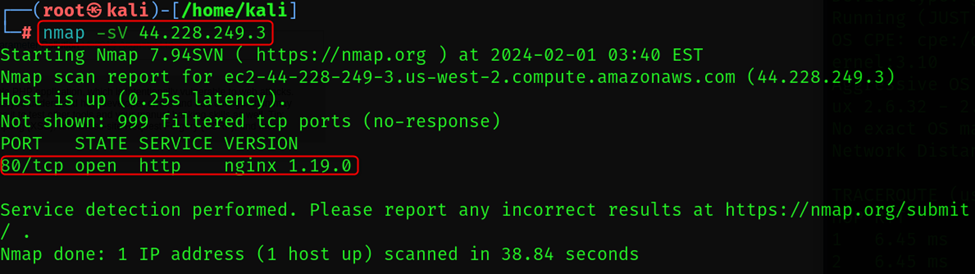
Service and Version Detection
-sV (Detect version of open ports )
Imagine scanning a network, not just identifying open ports, but also peering into the identities of the services running behind them. This is the magic of the Nmap -sV scan, a tool that goes beyond basic detection and unmasks the software versions lurking on open ports.
Advantages:
Enhanced Network Intelligence: Knowing the specific service and its version provides valuable insights. It helps assess potential vulnerabilities, identify outdated software, and understand the overall network architecture.
Prioritized Security Efforts: By pinpointing vulnerable services, you can focus your security efforts on the most critical areas, patching weaknesses and mitigating risks.
Disadvantages:
Increased Scan Time: Version detection requires additional probing techniques, making the scan slower than basic port scans.
Potential Intrusion Detection: Aggressive probing might trigger intrusion detection systems (IDS) or firewalls, raising security concerns.
OS Detection
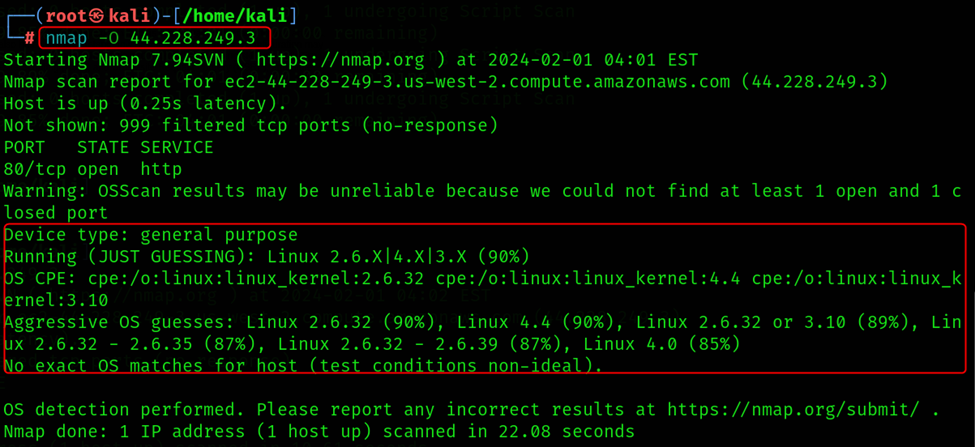
nmap -O
The shadows of a network, attempting to identify the operating system running on each host. Think of it like a digital detective, analyzing subtle clues in network responses to piece together the identity of the hidden system.
Advantages:
Network Profiling: Gain a deeper understanding of your network by knowing the different operating systems at play. This helps assess compatibility issues, potential security vulnerabilities specific to certain OS versions, and overall network heterogeneity.
Penetration Testing: In ethical penetration testing scenarios, OS detection helps identify specific exploits or vulnerabilities relevant to the target system, aiding in focused security assessments.
Disadvantages:
Limited Accuracy: OS detection isn't fool proof and can sometimes lead to inaccurate or inconclusive results. Factors like custom configurations, firewalls, and virtual environments can throw off the analysis.
Increased Scan Time: Compared to basic port scans, OS detection involves additional probes and analysis, making the scan slower and potentially resource intensive.